Not all viruses come from shady websites or downloads; some may lurk in seemingly harmless-looking emails – or more specifically, in the PDF files attached to them. A new report by cybersecurity firm Palo Alto Networks has revealed that PDF files are the most commonly used medium to deliver malware over email.
Such malicious emails are often paired with clever social engineering tactics for them to be successful. PDF files attached therein may use naming conventions used in a business context like “invoice_AUG_4601582.pdf” or “Updated Salary”, luring unsuspecting targets into opening these attachments. The attachments might also contain a URL link to click or a button that sends victims to a website with a malicious purpose.

 Even though .exe files are the top pick for malware once on a victim’s system, attackers are more likely to deliver malicious PDF files in email attachments. (Image: Palo Alto)
Even though .exe files are the top pick for malware once on a victim’s system, attackers are more likely to deliver malicious PDF files in email attachments. (Image: Palo Alto)
Malicious actors are not (yet) leveraging generative AI widely
Generative AI is a powerful tool that can be used for good or evil in the cyber realm. As the technology began to gather steam, especially since the launch of ChatGPT, experts wondered about its implications for cybersecurity. However, the Palo Alto Networks report has revealed that the technology has, in fact, not seen a significant increase in real-world usage by malicious actors.
 Grayware saw a huge spike following ChatGPT Public API release. (Image: Palo Alto)
Grayware saw a huge spike following ChatGPT Public API release. (Image: Palo Alto)
Regardless, traditional techniques attempting to take advantage of AI trends have led to a boom in AI-related scams. The researchers have noted that they’ve observed tremendous growth (17,818%) in attempts to mimic ChatGPT through squatting domains, which are website names that are deliberately registered to appear similar to a popular brand or product for the purpose of scams and adware. The AI chatbot’s popularity has also led to the emergence of grayware – software that falls between normal and malicious, such as adware, spyware, and potentially unwanted programs.
Constant battle with hackers creating pressure on security researchers
More alarming are the trends in the exploitation of vulnerabilities. According to the report, exploitation of vulnerabilities has increased by 55%, compared to 2021. Even Linux, which is considered to be a relatively secure operating system, is seeing a rise in malware targeting cloud workload devices. An estimated 90% of public cloud instances run on Linux.
The report highlights the cat-and-mouse game security researchers and hackers are locked in, where as soon as the former close the door on one vulnerability, threat actors already find the next open door to leverage. “This constant churn creates pressure on enterprise security teams attempting to protect their networks from bad actors exploiting those vulnerabilities,” notes the report.
OT (operational technology) systems, which are used in critical infrastructure industries such as energy, transportation, manufacturing, and healthcare, have also seen a worrying trend in malware. The report notes that these industries saw the average number of attacks experienced per customer in the manufacturing, utilities, and energy industries increase by 238%. Strengthening security with these systems is particularly important as any disruption “can have severe consequences for public safety, the environment, and the economy.”
Story continues below this ad
Cryptomining is another area of interest to threat actors. As many as 45% of sampled organisations in the research were found to be having a signature trigger history that contains cryptominer-related traffic. In fact, cryptominer traffic reportedly doubled in 2022.
 Bad actors are more likely to target people visiting adult websites and financial services sites. (Image: Palo Alto)
Bad actors are more likely to target people visiting adult websites and financial services sites. (Image: Palo Alto)
Interestingly, the report found that threat actors were more likely to target people visiting adult websites and financial services sites with newly registered domains (NRDs). NRDs are newly established websites and they tend to have weaker cybersecurity infrastructure as opposed to already-established websites. They are helpful for phishing, social engineering, or spreading malware.
Going forward, Palo Alto Networks expects the spread of malware through vulnerabilities to only increase, adding that evasive threats will become increasingly complex. “Organisations must therefore take a holistic view of their security environment to provide comprehensive oversight of their network and ensure security best practices are followed at every level of the organisation,” says Sean Duca, VP, and Regional Chief Security Officer at Palo Alto Networks.



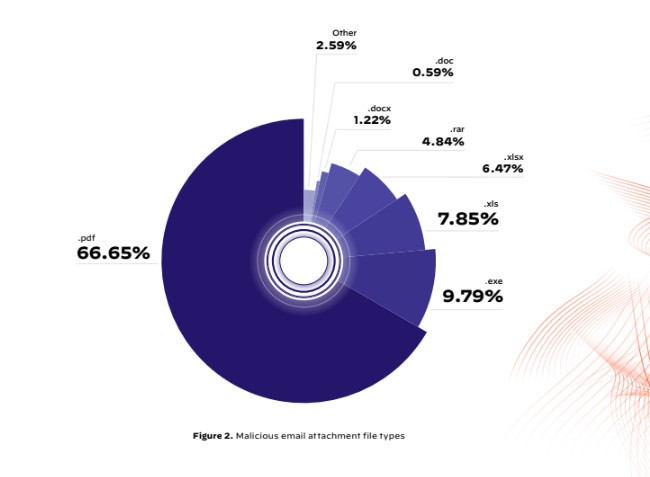 Even though .exe files are the top pick for malware once on a victim’s system, attackers are more likely to deliver malicious PDF files in email attachments. (Image: Palo Alto)
Even though .exe files are the top pick for malware once on a victim’s system, attackers are more likely to deliver malicious PDF files in email attachments. (Image: Palo Alto)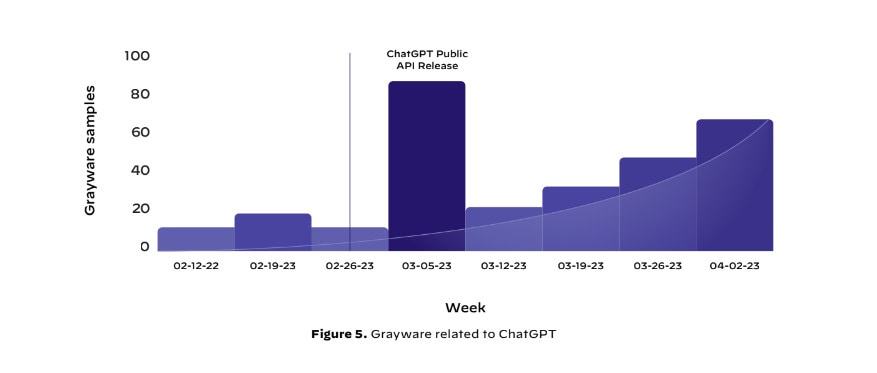 Grayware saw a huge spike following ChatGPT Public API release. (Image: Palo Alto)
Grayware saw a huge spike following ChatGPT Public API release. (Image: Palo Alto)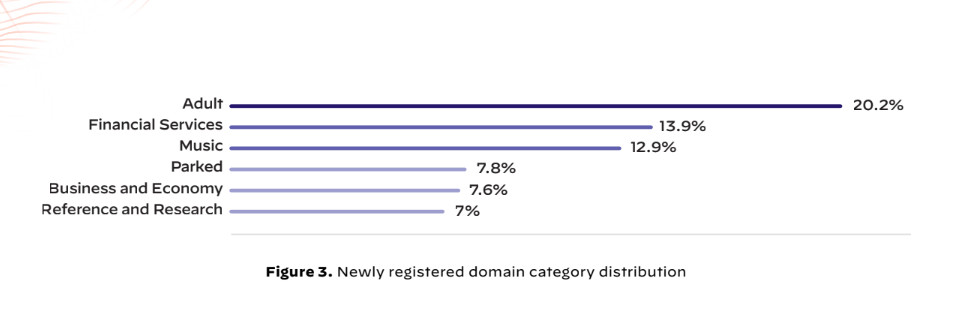 Bad actors are more likely to target people visiting adult websites and financial services sites. (Image: Palo Alto)
Bad actors are more likely to target people visiting adult websites and financial services sites. (Image: Palo Alto)





